The Best DefenseIs a Good Offense
The smarter way to stay on top of broadcasting and cable industry. Sign up below
You are now subscribed
Your newsletter sign-up was successful
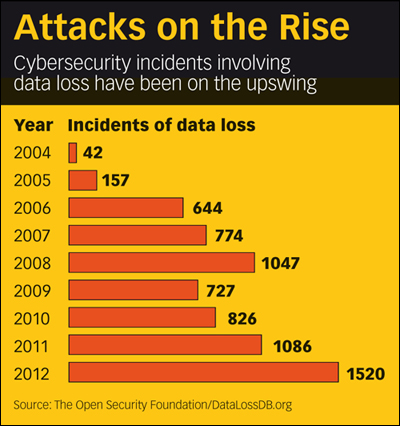
Cybersecurity attacks have been in the news almost weekly this year, with hackers sending bogus emergency alerts about an impending zombie atttack over several TV stations and major media companies including Apple, Twitter and Facebook all reporting security breaches. The Open Security Foundation noted that cybersecurity breaches hit record levels in 2012, with 1,520 incidents involving data loss.
But as media and entertainment companies face the rising threat of online security attacks, piracy and hacking, solutions for addressing the hazards are unlikely to be purely technological.
While experts point to a number of promising developments in chip security, fingerprinting and protection systems, they also stress that successful responses need to include some fundamental changes in the way companies educate their employees, organize their operations and formulate business strategies.
“The problem has definitely gotten worse,” says Peter Yared, CTO of CBS Interactive. “The vendors have improved the tools that are available [for preventing security breaches]. But at the same time, there is a growing hacker community. And the number of channels where attacks can occur has increased dramatically.”
“Compared to 10 years ago, companies have multiple presences beyond simply a website,” Yared adds. “They are now on the Web, Facebook, Twitter, YouTube, etc., and their employees have laptops, mobile and tablet devices that provide many entry points for attacks.”
The sheer range of potential threats for media companies also poses daunting challenges, with security experts pointing to dozens of different types of attacks. These include distributed denial of service (DDoS) attacks to shut down websites; viruses that infect systems with malware for collecting information; software flaws that give outside access to sensitive data; spear-phishing attacks on specific individuals within the organization; attacks on outside companies such as Twitter or Facebook that might provide passwords and other information about a company’s users; and pirates hacking into encryption codes for pay TV signals or DVD disks.
Governments and well-funded organized crime groups are increasingly involved in the attacks, but some of the most successful threats are low-tech tactics to steal passwords. Tom DeSot, executive VP and chief information officer at Digital Defense, notes his company is hired regularly by major corporations to test their defenses. In those tests, DeSot says, “we are successful in getting passwords about 95% of the time in social engineering attacks” that trick users out of their passwords via emails or phone calls.
Even higher success rates of 95%-98% occur when Digital Defense attempts to breach security from inside a company by going through desks or offices. Rogue employees or even cleaning workers often provide hackers with passwords using similar techniques.
Creating Best Practices
Here, education is the best defense, DeSot notes. But companies are increasingly using biometric tools that grant access based on !ngerprint or facial recognition technologies or a two-step login process. After a Web administrator logs in with his or her password, the employee then gets another randomly accessed password from a mobile app.
Progress is also being made in denial of service attacks, notes Neal Quinn, chief operations officer at Prolexic, a major provider of cloud-based service to protect against DDoS attacks. These typically involve networks of computers, or Botnets, that have been taken over by hackers to flood a website with so many requests that the site shuts down or slows down to the point where it is unusable.
“These attacks can also be designed to distract security people,” Quinn says, allowing hackers to penetrate the company’s defenses and steal sensitive information.
To defend against those attacks, Prolexic offers cloudbased services that make it possible to rapidly respond to attacks and handle large-scale attacks that would be difficult for a single company to repel. They have also built centers around the world to be closer to the sources of attacks, and they have extensive experience in identifying the nature of the breach. “A lot of it centers around human knowledge and understanding of the best countermeasures,” Quinn adds.
Likewise, companies have been improving the security of computer chips so hackers can’t steal encrypted pay TV signals, notes Paul Kocher, president and chief scientist at Cryptography Research, a major player in semiconductor security research and development. The company recently signed a deal for the use of its CryptoFirewall security core in EchoStar set-top box technologies. “We are in a period of rapid improvement in the underlying silicon used in these systems that will pay huge benefits,” Kocher says.
Better fingerprinting techniques are also helping companies find content that has been illegally posted on sites, notes Richard Atkinson, a well-known cybersecurity expert. A number of major companies have set up units to look for this pirated material on YouTube and other sites.
But Atkinson and others stress that technology is only part of the solution. “The industry has historically turned to lawyers and technology to solve piracy problems,” Atkinson says. He argues, however, that companies need to also pay closer attention on the “business process that encourages piracy” and revamp corporate cultures to better respond to threats. Traditionally, employees handling security “have been located somewhere in the bowels of the company” with little power to influence overall corporate practices, he notes.
To better combat the threats, companies should have someone who can directly communicate with the CEO about the threats and educate the company as a whole, adds Debra Sharon Davis, president and CEO of the Davis Communications Group.
Investing in these efforts, Davis adds, “isn’t cheap, but it is a lot cheaper than the alternative of having a company brought to its knees” by an attack that can “shut down its operation or damage its brand.”
For a look at how the government is planning to improve cybersecurity and some of the best practices for avoiding attacks, see Washington Watch.
E-mail comments to gpwin@oregoncoast.com and follow him on Twitter: @GeorgeWinslow
The smarter way to stay on top of broadcasting and cable industry. Sign up below
